Cryptography is a technique to provide message confidentiality.
• The term cryptography is a Greek word which means "secret writing".
• It is an art and science of transforming messages so as to make them secure and immune to attacks.
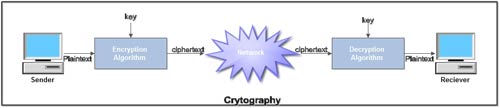
• Cryptography involves the process of encryption and decryption. This process is depicted.
• The terminology used in cryptography is given below:
1. Plaintext. The original message or data that is fed into the algorithm as input is called plaintext.
2. Encryption algorithm. The encryption algorithm is the algorithm that performs various substitutions and transformations on the plaintext. Encryption is the process of changing plaintext into cipher text.
3. Ciphertext. Ciphertext is the encrypted form the message. It is the scrambled message produced as output. It depends upon the plaintext and the key.
4. Decryption algorithm. The process of changing Ciphertext into plain text is known as decryption. Decryption algorithm is essentially the encryption algorithm run in reverse. It takes the Ciphertext and the key and produces the original plaintext.
5. Key. It also acts as input to the encryption algorithm. The exact substitutions and transformations performed by the algorithm depend on the key. Thus a key is a number or a set of number that the algorithm uses to perform encryption and decryption.
• There are two different approaches to attack an encryption scheme:
1. Cryptanalysis
2. Brute-force attack
Cryptanalysis
• The process of attempting to discover the plaintext or key IS known as cryptanalysis.
• The strategy used by cryptanalyst depends on the nature of the encryption scheme and the information available to the cryptanalyst.
• Cryptanalyst can do any or all of six different things:
1. Attempt to break a single message.
2. Attempt to recognize patterns in encrypted messages, to be able to break subsequent ones by applying a straight forward decryption algorithm.
3. Attempt to infer some meaning without even breaking the encryption, such as noticing an unusual-frequency of communication or determining something by whether the communication was short or long.
4. Attempt to deduce the key, in order to break subsequent messages easily.
5. Attempt to find weaknesses in the implementation or environment of use encryption.
6. Attempt to find general weaknesses in an encryption algorithm without necessarily having intercepted any messages.
Brute-force attack
• This method tries every possible key on a piece of Ciphertext until an intelligible translation into plaintext is obtained.
• On an average, half of all possible keys must be tried to achieve the success.